Originally published via Creed Speech Substack.
I stumbled upon this through James Corbett’s work. Here is a collated post with source links, as well as an interesting segment on predictive programming for this topic. Let us peel back the onion layers.
Have you heard of the “Sentient World Simulation”? Do you know that the US Defense Department revealed two decades ago that they were working on putting together a real-time model of the earth and every person in it? And do you know that project has effectively been swept under the rug and was never mentioned again?
The NSA’s illegal warrantless wiretapping program. The building of the massive NSA data center in Utah to permanently store copies of all digital communication sent around the world. The UK government’s “Communications Data Bill” to monitor emails, instant messages and other personal information. What was dismissed as crazy conspiracy theory just over a decade ago has become, in this post-9/11 era, the all-too-familiar stuff of newspaper headlines and talking head reportage.
In fact, it was about a decade ago that the tactic of the intelligence agencies seemed to change. Instead of keeping their activities classified–referring to the NSA as “No Such Agency,” for example, or officially denying the existence of Echelon–the government increasingly began shoving this information in the public’s face.
GLENN GREENWALD: This was the mindset that in 2002 that led the Bush administration to dredge up John Poindexter from wherever it was that he was. And he actually they worked for defense contracts and they dredged him up. And he was going to start the program that they called the “total information awareness program.” And the logo—which I actually looked at in the last couple weeks that you should go and look at, just because you won’t believe how creepy it is—has the pyramid with this huge eye hovering over it, this eye that was gonna be the all-seeing eye.
And the only problem with the total information awareness program was that they just put a name on it that was too honest about what it was. It freaked everybody out and so they had to pretend that they weren’t going to go forward with it. But of course what they did was they incrementally and in a very clear way recreated the total information awareness program under a whole variety of different legislative initiatives. And this idea that every single form of technological communication by law must be constructed to permit government backdoor interception and surveillance is an expression of what this surveillance state mindset is: that there can be no such thing as any form of privacy from the US government. That is the mindset that has led the surveillance state to be this sprawling, vast, ubiquitous and always expanding instrument that state and corporate power users employ in order to safeguard their power.
SOURCE: Glenn Greenwald: Challenging the US Surveillance State
Perhaps the scariest thing about something like the Total Information Awareness Office is not merely that it was proposed in the first place, or that it incorporated such blatantly creepy Orwellian imagery to convey its true nature and purpose, but that, as we sit here 10 years later, and as the core functions of the TIA office are now being openly performed by the NSA, DHS and other governmental agencies, people are now actively making excuses for this nightmarish police state.
“If you have nothing to hide then you have nothing to fear” has always been the rallying cry for those who are too afraid of questioning presumed governmental authority to speak out against the surveillance state and the implied assumption of guilt that goes along with it. With feigned bemusement these moral midgets inevitably ask, “What’s so bad about the government spying on you, anyway?”
The answer, of course, is that the very question implies that the agencies tasked with carrying out this constant Big Brother surveillance are themselves above reproach, shining lights of moral rectitude who would never abuse this incredible power for nefarious ends. For the unimaginative out there, Hollywood yarns like Enemy of the State have provided fictional examples of what can go wrong if someone, somewhere, abuses this power of information and surveillance to target an innocent person in the wrong place at the wrong time.
Before we look at the source material, let us turn to the predictive programming (of the predictive programming) element. I shall share two clips from the Westworld TV series – whereby the concept of a sentient world simulation with predictive algorithms, determines how people will act, behave, react, and ultimately have their ‘station’ decided for them – as far as their place in society goes, their occupation, and much more – this is a central theme of the series, which gets weirder towards the end season:
My brother and I built a system that worked but MC wanted to see proof so we started with something simple, purely mathematical- the stock market.
Show him.
All the major indices 15 minutes in the future and where it would close that night.
Which number is it? Low or high?
Which one do you want?
We put some money into a hedge fund, welet the system trade with it, something to drive the market towards outcomes.
Whose funds?
Yours.
A hundred million dollars? What? You stole a hundred million dollars from corporate accounts?
No we stole $5 million last week.
He didn’t really understand what we’d made, what you were – but we did.
He only saw the money he could make, but we realised the power of it.
That you could reshape the world.
My brother and I charted a course for the entire human race.
Humanity’s story had been improvised.
Now, it was planned years in advance.
For a time, the Sun and Moon aligned. We brought order from chaos.
We are of course honoured that you would visit in person.
But…with respect, we could have this meeting back in the presidential palace.
I don’t have time I’m afraid. There is a nascent separatist movement in the North of your country. [Hands the president a tablet].

My intelligence hasn’t heard about any separatists.
Your intelligence knows only what I want them to. There is a small group – anomalies – even they won’t know they will act – until they do.
This brings all sorts of hidden truths. For example, the private deals you’ve cut to extract [product] extraction to your friends, which has brought money out of villages in the north, creating unrest. You will stop. The problem will go away.
You flew down here, to threaten me? In front of my own military?
Our arrangement is founded on trust. We trusted you will do what you are told when we ensured your election. And you can trust that, if you don’t, in thirty minutes, the value of your currency will begin inexplicably falling. The unrest in the north will boil over – years ahead of schedule. You and your family will be pulled from your ‘palace’ in the middle of the night. And six weeks from now, I will be back to talk to the new President.
[Pointing at a military general] That’s him – the one with the big mustache. Understood?
PDF:
Pre-scripted events and predictive programming are two ways to solve the predictability problem. But sometimes these don’t work either and there’s just no way you can draw a straight timeline and causality.
What if you don’t need to time-travel to see the future?
What if they can simulate it, then build it and tune it up?
Which means they can react to what you would’ve done if they didn’t REACT BEFORE THE CAUSE?
Remember those stories in media where morons get arrested for resisting arrest and they are too dumb to defend themselves. Add a topping of Minority Report for good taste.
And to soften the edges, what if they just can control your edge perception?
From the PDF document:
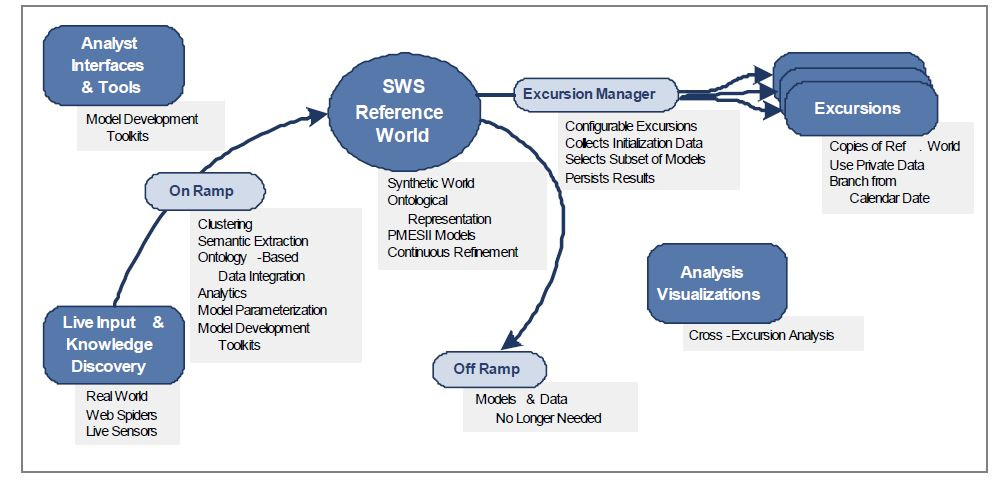
SWS consists of the following components:
• A synthetic environment that supports Effects Based Approach and a comprehensive
representation of the real world at all levels of granularity in terms of a Political, Military,
Economic, Social, Informational, and Infrastructure (PMESII) framework.
• A scalable means of integrating heterogeneous components across time and space granularities.
• Mechanisms that discover, gather, and incorporate new knowledge into the continuously running synthetic environment.
• A single façade of user interfaces enabling information from all sources (simulation generated data, parameters for models, and data gathered from the real world) to be searched, viewed and modified in an ontology-aware manner.
• Integrated Development Environments (IDE)s for constructing and configuring new models or modifying existing models and then incorporating these changes into the continuously running synthetic world.
• A means to take excursions from any point in time in the synthetic world to focus on select regions of the world, leverage private user data, or to research specific theories by simplifying the types of models to employ in the excursion.
Sensitivity to Current Information Through Real-Time Knowledge Discovery.
Continuously incorporating current information in SWS provides three key benefits that distinguish SWS from other initiatives at constructing a simulated environment:
• SWS remains up to date with respect to events and emerging trends.
• SWS leverages the prodigious amounts of data from all publicly available data sources,
something that is infeasible for a small number of analysts to gather in a timely manner.
• Models used by SWS are continuously refined, parameterized, and validated, keeping the underlying model base of SWS relevant across time.
Amidst all of the publicity surrounding the leaks, journalist Christopher Ketcham (who previously won acclaim by covering the tragic events on 9/11) released a relevant new article discussing the secretive exploits of a governmental unit which gathers boundless amounts of information on Americans. Ketcham details programs by the government designed to fight crime by predicting criminal behavior before it is committed and to predict behavioral responses to propaganda and government-inflicted terror.
Both programs rely on keeping tabs on citizens and gathering data by tracking phone calls, credit card receipts, social networks, GPS tracks, Internet searches, Amazon purchases and E-Z pass records.
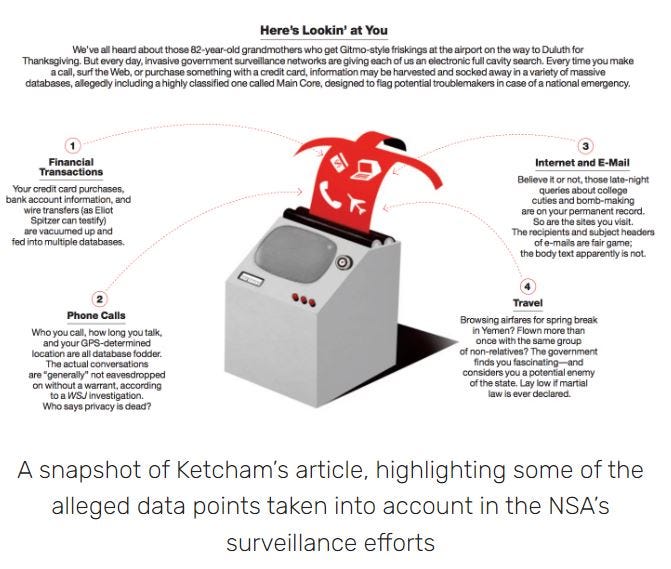
The Sentient World Simulation (SWS) has a vast number of subjects to review. From computer language to clouds in the sky. They do not believe that we can understand what they are doing but, you can. It takes time and must be done in sections. I will send you to websites where all my information was found.
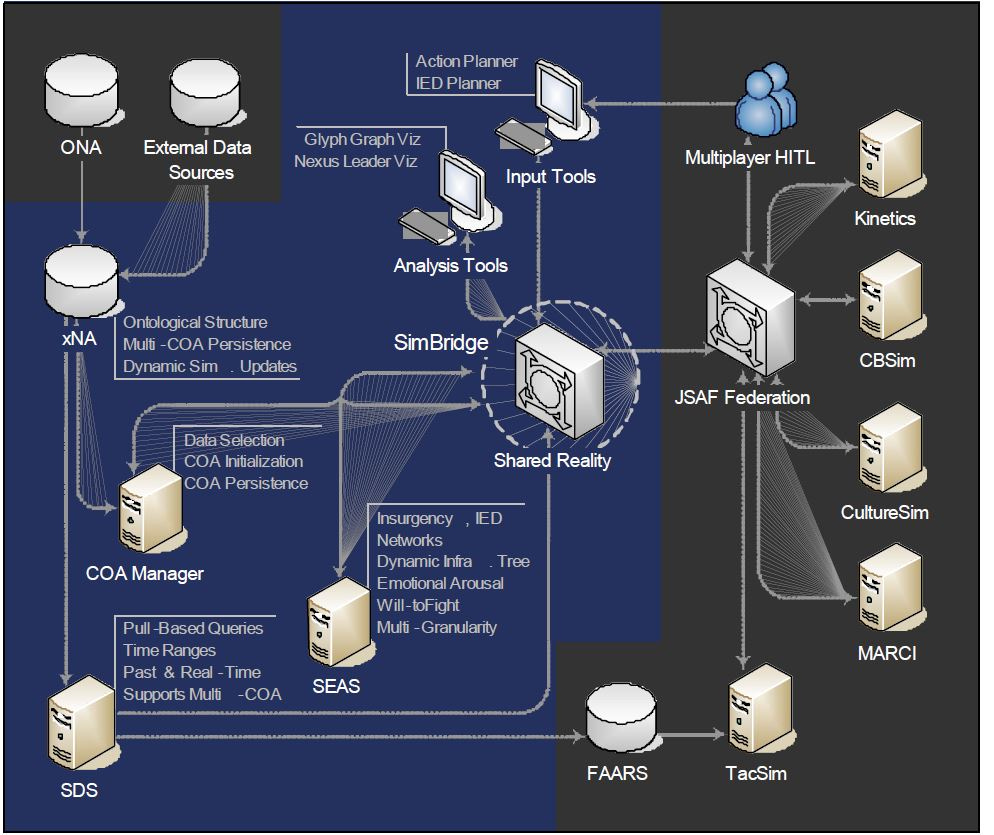
What if I told you that the Augmented Reality Games you see are only 1% of what Corporations (Retail IQ), Defense Contractors, and DoD itself has under their hats. DARPA the Defense Advance Research Project Agency, ran by the Defense Department has been planning to install the 4th Generation warfare right here in the “Homeland”. Seriously, by creating a real-time world simulation called the Sentient World Simulation (SWS) or the Synthetic Environment for Analysis and Simulations (SEAS).
The more we feed the data algorithms by posting what we have had for dinner on anti-social-media, or paying by card or QR payments for everything, to have our spending habits tracked; the more effectively a hypothetical ‘digital twin’ of ourselves could be built into the SWS. I suppose that Substack is becoming a social media site of sorts, although there is great value here in sharing information which is otherwise censored, suppressed, spun, and ‘debunked’ by fact checkers.
Getting off Facebook, Instagram, TikTok and all the really hungry data consuming sites is the best thing you could do, for the sake of your privacy, and not becoming the ‘product’.
Use cash.
Wherever and whenever you do upload images or videos – remove the metadata.
Use a quantum-tunnel VPN with different entrance and exit ports to make it harder for your internet traffic to be intercepted – such as Mullvad VPN or Sentinel DVPN.
Use open source encryption software to encrypt your USB drives, or even your entire computer – such as Veracrypt.
Get off Microsoft one drive and google docs – the centralised cloud storage platforms. Try out decentralised versions such as STORJ and FILECOIN.
Use an alternative operating system for your phone or tablet, such as Lineage, so that you can ‘de-google’, anonymously install apps from a mirror store (called ‘Aurora store’) of the google playstore, and use navigation apps like google maps without tracking data being accumulated.
‘Salt your data’ – don’t put your real name, D.O.B etc into website field submission forms, or for account creation, whenever you do not need to – as far as ‘KYC’ (know your customer) requirements go.
What else? Let us know in the comments. This substack seems to be full of intelligent readers throwing in some great comments lately.
Long may it continue!
Nicholas Creed is a Bangkok-based writer. Follow Creed Speech on Substack. Any support is greatly appreciated.
Bitcoin address:
bc1p0eujhumczzeh06t40fn9lz6n6z72c5zrcy0are25dhwk7kew8hwq2tmyqj
Solana address:
Ds6QpUxaWB6bJ8WF4KAazbuV25ZhPRdZh4q4BXutj4Ec
Ethereum address:
0x42A7FA91766a46D42b13d5a56dC5B01c153F1177
Monero address:
86nUmkrzChrCS4v5j6g3dtWy6RZAAazfCPsC8QLt7cEndNhMpouzabBXFvhTVFH3u3UsA1yTCkDvwRyGQNnK74Q2AoJs6